How to find breached email IDs and passwords.
How to find breached email IDs and passwords.
Hey there!!!
NOTE:
ALL INFORMATION IS OPEN SOURCE. IT'S ALL ETHICAL. THE INFORMATION IS ALREADY AVAILABLE ON THE INTERNET IT'S JUST A WAY TO FIND IT OUT
To find email id using theharvester tool and then analyzing them with maltego (a kali linux tool like the harvester)
So for searching email ids open Linux terminal and insert the following commands
# theHarvester -d gmail.com -l 500 -b yahoo
Where
[-d ]
is for our target you can give any domain like yahoo or the AOL or any other.
[-l]
Is for list, the number of results we wanna scan it's not mandatory to mention.
[-b]
For the search engine which should be used like shodan, Google, yahoo and there are many.
You can use the all command to search in all available search engines, as follows :
# theHarvester -d gmail.com -l 500 -b all
Now have some patience it'll give you some results .
Harvester's work is complete now.
You can read more about it from
 |
Now copy some emails and create another file with a .csv extension
It'll be used later.
Now coming to maltego (software developed by PATERVA for using in OSINT and providing APIs or discovering data from open source)
If you are using it for the first time an account is needed. So for the same either you can make one in the kali Linux community edition(pre installed) or login with credentials in the given website.
click here for login credentials..
If you're not using kali Linux or wanna know more refer to this article
Well okay! moving on.....
 |
After this install Haveibeenpwned transform/ API within maltego luckily which is free.
 |
Now click on create a new graph:
 |
Now click on import/ export option:
Import graph from table:
 |
..... on next :
Chose your .csv file where you stored your emails obtained from theHarvester :
Obvious the next button:
 |
By default this will be on sequential but set it to manual.
 |
Next.......
 |
Finally smash the finish button:
 |
Now something like this will open up, you can zoom in and out by the mouse wheel.
These small colored circles represent email ids if you zoom it'll be visible.
 |
Select them according to your will.
Difference between selected and non selected is clear in this picture.
 |
Now right click after selecting and search havei....... only this much then rest will be visible automatically
 |
And select get all breaches of email addresses.
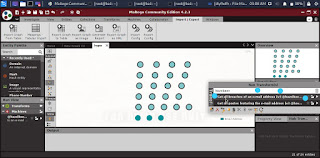 |
After a min. or two this type of design or interface will appear depending upon number of emails scanned.
Now from this you will get the breached emails (if any in the list).
 |
Time to get passwords of some.
So now like earlier in steps 3rd or before create a new graph , import your file, select it and then on right click and searching for havei........ select second option which says get all pastes(by paste i mean you will get the plain text files url in which the password of breached email id is saved) from internet in which the passwords of email Ids are saved.
 |
Before this step analyze the screen like which color represents emails which one represents nodes which one gives you the link of files in which email Ids and passwords are saved to already hacked databases.
And double click to get the link and now copy the link paste in any browser and the file would be opened.
The link containing file would be something like this on zooming in it.
After pasting the url in browser the list could be like this.
End!!
It was quite lengthy but it's amazing have a look.
Secondly if you got stuck in any step then contact me we'll discuss it together, the thing is little alien to me, too.
I or any other any contributor of the blog is not responsible for anything done unethical by you. This post was only for information and for educational purpose about tools present in kali Linux nothing more than that.
I just searched the internet and used it myself and came across this stuff
So give it a try
~Invincianon